pfSense® vs OPNSense - which firewall OS is better?
Article last updated on July 28, 2020.
Disclaimer:
I, the author, have no affiliation or relationship with either pfSense or OPNSense. I don't know anyone working on either projects or companies behind these projects, nor do I make any money from either project.
I'm a software engineer, working on a completely unrelated open-source project. The article below is my own opinion, which I developed based on my 5+ years of experience using both systems.
In this test, we are comparing the latest releases of both operating systems pfSense® 2.4.5 with OPNSense 20.1.
pfSense® 2.4.5-p1
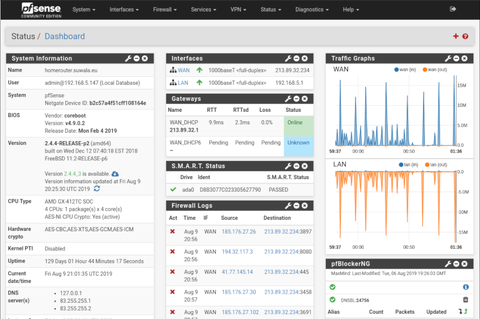
OPNSense 20.1.7

History
Before we jump into functionality, security, and usability, let's look at the relevant parts of the history of both systems.
Both systems have a common ancestor - m0n0wall.
pfSense forked m0n0wall in 2004 and released the first version in 2006.
OPNsense forked pfSense in 2015, right after m0n0wall got discontinued.
It's worth noting that when m0n0wall got discontinued in 2015, Manuel Kasper, the author or m0n0wall recommended its users to migrate to OPNSense rather than pfSense.
Reasons for the OPNSense fork
OPNSense lists their reasons for forking pfSense here https://docs.opnsense.org/history/thefork.html
The main reasons are:
- code quality
- regular releases
- security issues related to the web UI being run as root
- source code for the pfSense build tools is are no longer publicly available.
- concern regarding transparency, new ownership of the pfSense brand, using the brand name to fence off the competition.
- several license changes for no apparent reason
pfSense developers call these reasons bogus.
I'll analyze these claims below.
About the code quality
I personally don't have an opinion about the code quality because I haven't worked on either project. pfSense claims that OPNsense has more bugs, and therefore the quality of OPNSense is worse. OPNSense claims the opposite.
About the regular releases
I agree that more regular releases are desirable from the security perspective.
I examine this in detail in a section below.
About security issues related to UI being executed as root
pfSense runs the PHP-based web UI under a root user. That sounds like a bad idea to me.
They claim that it's unavoidable since almost all actions require root privileges. In my opinion a proper sudo configuration would be preferable to running everything as root, but perhaps the complexity involved is much greater than the benefits of doing so.
OPNSense claims that they forked the project to not run the Web UI under the root user, but when I look at it myself, the lighttpd and PHP are running in OPNSense as root as well. I'm either missing something or there's some false advertising on OPNSense's part. Perhaps they are working on making this change, but if that's the case, this should be clearly stated as currently it's implied that OPNSense doesn't run the web server as root.
About the build tools being taken away
IMO this is the most legitimate reason for forking the project. If the build tools for pfSense are not open-source then, in my opinion, the entire project is not fully open source either. Apparently, it's possible to apply to ESF to receive the source code for the tools, but that's a very bizarre way of holding power over the source code while claiming that it's open source.
About transparency, new ownership and fending off competitors
Based on the fact that some of the source code has been taken away I agree about the lack of transparency.
From my perspective, it looks like pfSense people got frightened that the source code is getting forked by OPNsense and tried to make the fork more difficult by taking away some of the code.
I also agree that Netgate is using their pfSense trademark to discourage users from running pfSense software on hardware from other vendors.
I understand that building open-source requires money, and the project must make enough to continue, but certainly, there are better ways of solving this. I just wish that their business strategy would be to compete on better products or better service, and not to flash a trademark badge. Recent popups saying "Absolutely No Commercial Distribution Is Allowed" is really against the open-source spirit (if not against the actual rules).
About the pfSense open-source license changes
Both systems are open source but have different licenses. pfSense is currently licensed under Apache 2.0 license while OPNsense uses the 2-clause BSD license. From the end-user perspective, these licenses on their own are very similar.
There's much controversy around the pfSense license changes. I went through the rabbit hole of the web archive to look at the history of these changes. As far as I can tell, the license of the pfSense project changed 4 times between 2005 and 2019.
The original license from 2005: 3-clause BSD license
- Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
- Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
- Neither the name of pfSense nor the names of its contributors may be used to endorse or promote products derived from this software without specific prior written permission.
In 2010 the third clause got dropped, and the license became a 2-clause BSD license
- Redistributions of source code must retain the above copyright notice, this list of conditions and the following disclaimer.
- Redistributions in binary form must reproduce the above copyright notice, this list of conditions and the following disclaimer in the documentation and/or other materials provided with the distribution.
The license dropped the third clause, becoming more permissive.
In August 2014 the license changed to a 6-clause non-standard ESF license.
I won't quote the entire license, only the relevant part. The license restricted the use of "pfSense" brand.
Products derived from this software may not be called "pfSense" nor may "pfSense" appear in their names without prior written permission of the Electric Sheep Fencing, LLC.
In July 2016 the license changed again to a standard Apache 2.0
The relevant part is:
This license explicitly states that it does NOT grant trademark rights, even though licenses without such a statement probably do not grant any implicit trademark rights.
In my opinion, all these licenses are totally fine. There's nothing wrong with either one. It makes sense to protect the brand name by a trademark as well.
The controversy is around the way the trademark is being enforced by the pfSense project. Sometime in 2018, the following popup started showing up in the web interface
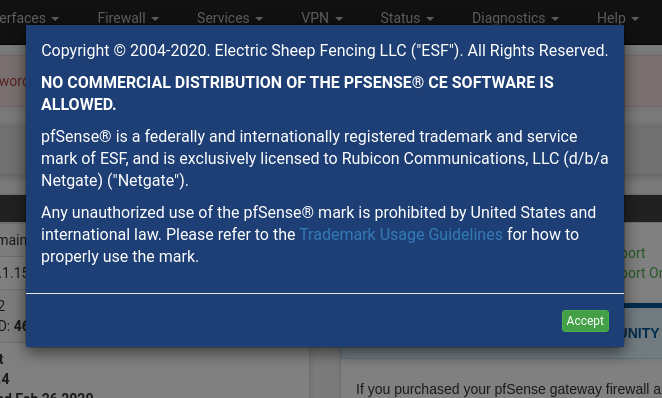
Saying "All rights reserved" and "No Commercial Distribution Is Allowed" is in my opinion rather unusual for an open-source project, and goes against the open-source spirit. Many users got concerned.
According to the pfSense documentation
The Apache 2.0 license only applies to the software and not the pfSense name and logo, which are trademarks and may not be used without a license.
and
... guidelines do not permit someone to offer “Installation of pfSense® software” as a service ...
My understanding of the Apache 2.0 license and "fair use" is different, but that's only my opinion, I'm not a lawyer.
Apache 2.0 license permits commercial distribution (as do all open-source licenses). So the "trademark guidelines" from pfSense are limiting the software license. I would like to hear from someone independent who knows the copyright/license/trademark laws to tell me if this trademark guideline is compatible with the Apache 2.0 license.
I'm just a software developer but my understanding of the fair use trademark law is that using pfSense name to describe service of installing the operating system is also permitted by law.
Numerous threads appeared on Reddit and other forums pointing this out.
- [1] https://old.reddit.com/r/PFSENSE/comments/7398pa/absolutely_no_commercial_distribution_is_allowed/
- [2] https://old.reddit.com/r/opensource/comments/743tvy/pfsense_is_free_and_open_source_so_it_should_not/).
- [3] https://www.reddit.com/r/PFSENSE/comments/7398pa/absolutely_no_commercial_distribution_is_allowed/dnoxaw8/?utm_source=amp&utm_medium=&utm_content=comment_timestamp
Most clearly it has been stated here by one of the main pfSense developers:
Basically, don't take what we build and make available for free, and use it to compete with us.
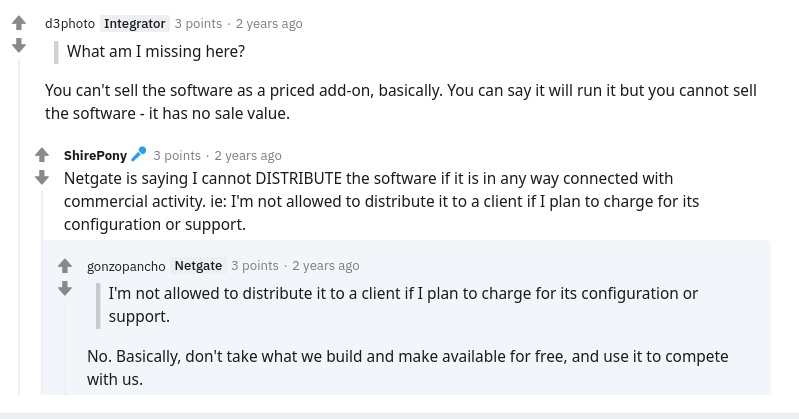
uff... I understand the need for making money, but this looks like the company wants all the benefits of claiming open-source without giving people any rights that come with open-source.
About the OPNSense license
Here the situation is much simpler. OPNsense is licensed under BSD 2-Clause "Simplified" License and the OPNSense website makes the license crystal clear by saying:
We like the BSD license, a simple two clause license that gives freedom to the audience we want to serve. It basically gives you the right to do whatever you want to do with the code, even fork it and take it from there.
More importantly, there are no additional trademark restrictions. Quite the opposite.
1. The name and logo may be used to promote OPNsense based products or services.
2. The name and logo may be used to promote or serve OPNsense or related projects and their communities.
This is what most people think about when they hear "open source".
Politics, drama & bad blood between the two projects
This has nothing to do with technology, so if you don't enjoy reading about flame wars, move on to the technical section.
It's impossible to not mention the elephant in the room - the bad blood between pfSense and OPNSense.
In 2016 one of the Netgate/pfSense developers took over the opnsense.com domain to insult the competing project. For a time the opnsense.com displayed a "satirical" video from the movie Downfall (depicting the final days of Adolf Hitler and Nazi Germany). The site was full of vulgar language describing the OPNSense software. This ended after WIPO ruling:
In November 2017, a World Intellectual Property Organization panel found that Netgate, the copyright holder of pfSense, had been using the domain opnsense.com in bad faith to discredit OPNsense, a competing open source firewall forked from pfSense. It compelled Netgate to transfer the domain to Deciso, the developer of OPNsense.
More information about this incident, including the website snapshot, can be found on https://opnsense.org/opnsense-com/
Before writing this article I spent an entire day reading various forum threads and it's clear that there's no love between the two projects. There's plenty of antagonization of OPNsense on pfSense forum as well as various subreddits.
I have not seen the same behaviour from the other direction - if you have, let me know so I can add it here for some balance.
The pfSense folks also took over /r/opnsense and refused to give it back to the OPNsense project, created /r/OPNScammed to badmouth the competition. This drama never ends - if you are interested, start reading here
Technical comparison
Now, let's leave all the drama behind and look at the technical aspects of these projects. After all, this is why I started writing this article in the first place.
Security
It's hard to make any definitive statements about security, but we can look at a few different aspects of each project to understand the basics.
Operating system security, patching frequency and known vulnerabilities.
Base Operating system
pfSense 2.4.5-p is based on FreeBSD 11.3.
OPNSense 20.1 is based on HardenedBSD 11.2.
HardenedBSD is a security-enhanced fork of FreeBSD. The HardenedBSD Project is implementing many exploit mitigation and security technologies on top of FreeBSD, and therefore should be more secure than the regular FreeBSD.
In this respect, OPNsense has an edge over pfSense.
Security Vulnerabilities
I tried to look up the CVEs for each project to see if there are any currently active vulnerabilities. There were no major incidents in either project. pfSense has a longer history so there are more historical entries, but that's expected.
As far as I can tell, both projects are the same in this aspect.
Update frequency
Another important security aspect is how quickly are the security patches released to address known vulnerabilities.
pfSense - update frequency
From their documentation:
Releases are made when they are ready. A public schedule is not available at this time, but release announcements and progress messages are made on the Netgate Blog.
We provide maintenance releases as needed, typically a couple per year. These include primarily bug fixes and security updates.
From the blog, I see that the last releases were:
- 20 Dec 2019 - current date (7 months since the last release)
- 20 May 2019 - 2.4.4-RELEASE-p3 (5 months since previous)
- 07 Jan 2019 - 2.4.4-RELEASE-p2 (1 month since previous)
- 03 Dec 2018 - 2.4.4-RELEASE-p1 (3 months since previous)
- 24 Sep 2018 - 2.4.4-RELEASE (4 months since previous)
1 Major release and 3 minor releases in 15 months.
pfSense project aims to release "when it's ready", so this release schedule is understandable.
I wish for a little more frequent releases to patch security issues, but on the other hand, I think this schedule isn't too bad.
OPNsense - update frequency
OPNsense has a different update strategy than pfSense.
From their documentation:
OPNsense’s update schedule consists of two major releases each year, which are updated about every two weeks.
From the blog I see that the last releases were:
- 19 Dec 2019 OPNsense 19.7.8 released
- 26 Nov 2019 OPNsense 19.7.7 released
- 01 Nov 2019 OPNsense 19.7.6 released
- 15 Okt 2019 OPNsense 19.7.5 released
- 03 Okt 2019 OPNsense 19.7.4 released
- 29 Aug 2019 OPNsense 19.7.3 released
- 05 Aug 2019 OPNsense 19.7.2 released
- 25 Jul 2019 OPNsense 19.7.1 released
- 07 Jul 2019 OPNsense 19.7 released
Holly cow, that's a lot of releases. 9 releases in 6 months feels a little overwhelming.
On one hand, I'm glad that all the security fixes are being done quickly and released to users frequently, but on the other hand, I would rather not update routers every 2 weeks if there's no are no security issues!
I would wish for a balance between these two release schedules. Perhaps 1 major release every year and 1 minor release every 2 months unless there's an urgent security vulnerability that needs patching right away.
I guess you still can update every 2 months even though OPNSense is released every 2 weeks.
From the update perspective, OPNSense wins.
pfSense security
- Infrequent releases
- Based on FreeBSD (neutral)
- No major security incidents in recent time
In my opinion both systems are secure, but OPNsense has a slight edge because of frequent security updates and HardenedBSD.
OPNsense security
- Frequent releases
- HardenedBSD instead of FreeBSD
- No major security incidents in recent time
Release notes and update experience
This is a bit of a rant, but I think release notes matter.
Looking at the pfSense 2.4.4 release notes it's clear what has been changed and details are clearly described. I very much like this amount of information. They clearly spend appropriate amount of time writing these information.
OPNsense's 19.7 release page is considerably poorer. We get a bullet-list of commit messages. It's clearly not a priority for them to write release notes.
pfSense has a very rudimentary interface for making system updates. When a new update becomes available you can see that the version has changed, but you don't get to see the details - you have to go to the blog to read about it.
OPNsense displays same release notes (although short) in the web interface and on the website. This is great because you can read about the changes that are about to happen.
The upgrade process can be shaky for both systems. Both pfSense and OPNsense crashed for me several times during the upgrade procedure. This is often blamed on third-party plugins and packages. Both systems recommend making a full backup before the upgrade procedure.
pfSense
Great release notes in the docs!
Poor information in the update web UI
Upgrade procedure can be shaky
OPNsense
- Very rudimentary release notes
- Good update interface with decent amount of information
- Upgrade procedure can be shaky
Performance
Both systems are based on BSD, both use pf as the underlying firewall and share many of the same packages, therefore the performance is nearly identical. Nothing to say here.
I've executed routing and VPN benchmark on both systems. In all my tests, the results are identical.
Functionality
pfSense and OPNsense share most of the functionality. Both systems are very similar. Both systems also have the same hardware compatibility.
One thing that I miss in OPNSense is the "Execute Shell Command" functionality in the web interface. pfSense has it, and it's most useful when dealing with some edge cases. I routinely use it to update the BIOS on routers.
I won't list all functionality that is identical, instead I'll focus on the differences.
pfSense - unique functionality
- Support for the ZFS filesystem (see stability section for details)
- pfBlockerNG package is a reason why many users stick with pfSense
- email notifications for new clients (better security monitoring)
- Snort and Suricata packages are available (OPNsense has only suricata)
- Execute Shell Command in the web interface
OPNsense - unique functionality
- Wireguard VPN (pfSense still doesn't have it)
- More plugins (I counted 75)
- Automatic, encrypted system backups to GoogleDrive or NexCloud
Documentation and online resources
Both projects have rather large documentations.
pfSense has been around for much longer so it's not surprising that their documentation is larger and more complete. There are also much more online resources in terms of Youtube videos, blog posts and tutorials on almost any subject. if you are not sure how to do something in pfSense, you can easily find third-party information somewhere on the internet.
OPNSense has good documentation, but in comparison to pfSense it's smaller.
When some information is missing, it's often possible to piggyback on pfSense's docs to find information about how to do things in OPNSense. Both systems are very similar in functionality so docs often apply to both.
Here pfSense wins without breaking a sweat.
pfSense
- bigger documentation
- more online resources
OPNsense
- Smaller documentation
- Users sometimes must piggyback on pfSense's documentation
- Fewer online resources
Community and support
Here again, the number of pfSense users is much larger. In this aspect, pfSense wins again.
On the other hand, I have to say that OPNSense forum is much, much friendlier, and has that "open-source" feeling to it. Netgate forum feels more corporate and restrictive.
It's not uncommon to be banned on pfSense forum for asking a wrong question or have a topic removed because it doesn't follow the forum guidelines. Running pfSense on anything but Netgate hardware is frowned upon.
I have not seen the same behaviour on the OPNSense forum - people that run OPNsense on hardware not delivered by Deciso aren't unwelcome.
One nice aspect of the OPNSense community is that in a short period of time it developed tons of community plugins. At the time of writing, I counted 70 different community-contributed plugins.
It's going to be interesting to see how this situation changes over the next couple of years. Will the pfSense forum become friendlier? Will OPNsense catch up in the amount of online resources?
pfSense
- larger userbase - larger community
- less friendly forum
- More restrictive rules on the forum about what questions are acceptable. "Enterprise" spirit (subjective)
OPNsense
- Smaller userbase - smaller community
- More friendly community
- "Open-source" spirit in the community (subjective)
Stability
I haven't seen any major stability issues from either project. In my opinion, both systems seem stable and solid.
OPNsense has more updates, so there's a greater risk of something going badly during an upgrade, although I haven't experienced any in the last 12 months.
From reading forums I gather that IPS/IDS software based on Suricata seems more stable in OPNSense. (not my personal experience, as I don't use it).
pfSense folks claim that VLANs have been broken in OPNSense for a long time. This is probably true, but I have not been affected by it myself.
What makes pfSense more stable in some cases is the support for the ZFS filesystem. The default UFS filesystem used by both pfSense and OPNsense can become corrupted during a power outage. At the moment OPNSense supports only USF while pfSense supports both.
I would say that pfSense has a slight edge on stability in comparison to OPNSense.
User experience
Software is not only about functionality. The ease of use also matters.
In my opinion, usability is the major difference between these two systems.
OPNsense reimplemented the entire front-end interface from scratch and I think they did a decent job. The UI looks more modern and is organized in a way that makes more sense.
My favorite gotcha in pfSense is the location of the "power off" and "reboot" options. If you have not used pfSense before, I bet it would take you quite a while to find it. It's buried in the middle of the "Diagnostics" menu. Why diagnostics and not "System" or in the right corner where the "logout" is? ¯\_(ツ)_/¯
If you are not used to the BSD jargon you will be surprised to find that "power off" is called "Halt".
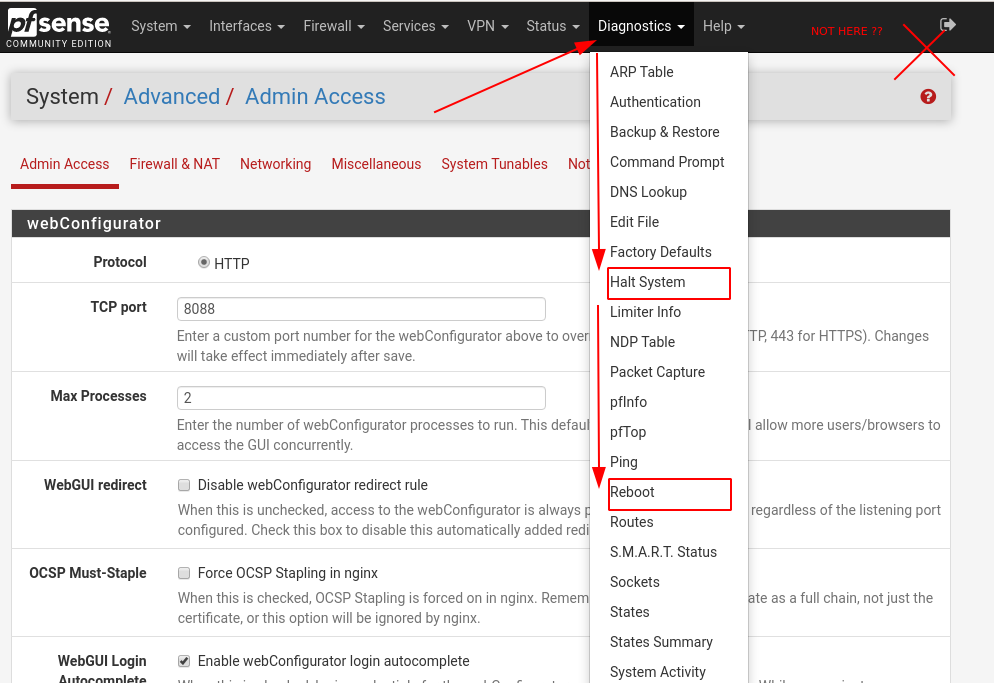
In OPNSense the power options are as clear as they should be.
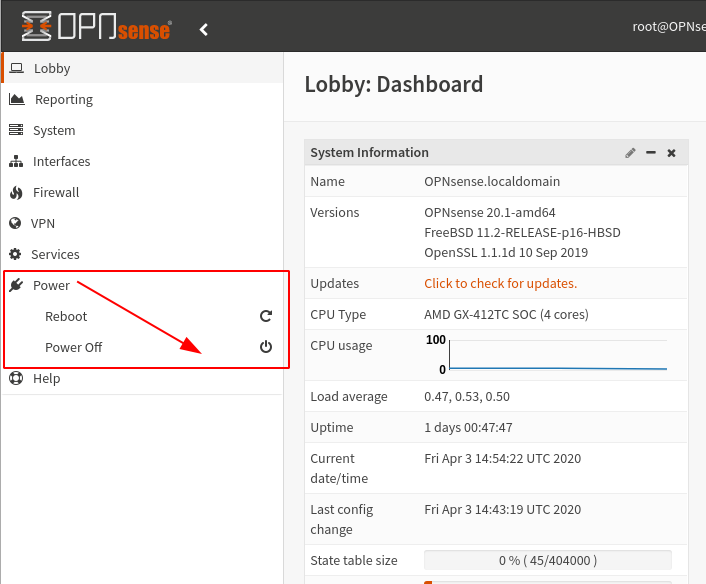
In OPNSense, if you don't know where a certain menu element is, you can search for it.
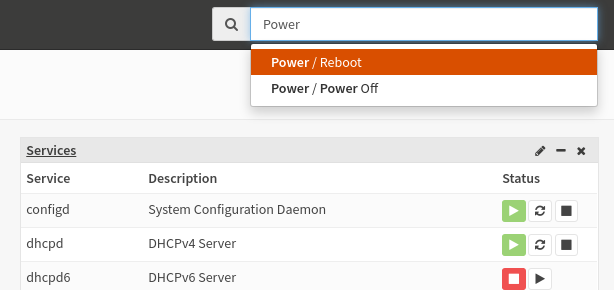
However, not everything is covered by the search functionality. In many cases, you still have to manually search for it yourself. For example typing, "ssh" returns 0 results, even though the option is available in the system. I hope they keep working on it because the ability to search is really useful.
pfSense
- worse organization the user interface
- lack of search bar
- worse OS update interface
- trademark popups after every update
- Ability to execute shell commands from the web UI.
OPNsense
- Better organization of the user interface
- Search bar (unless it doesn't work)
- better OS update interface
- no trademark popups!
- lack of "Execute Shell Command" functionality
Final conclusions
I'm glad that we have two strong open-source systems competing with each other for the router market. From the consumer perspective, it's never good to have a single player dominating the entire market.
Aside from small differences, the systems offer largely the same functionality, performance and hardware compatibility.
OPNSense shines when it comes to user interface and usability. pfSense shines when it comes to the amount of documentation and online resources. OPNsense has slightly better security due to HardenedBSD and more frequent releases.
pfSense has slightly better stability due to fewer releases and ZFS support.
Whichever choice you make, you will be happy with the result.